MFA for Improved Security.
See How it Works. Demo Now!

Digital transformation, remote work, and the cloud have accelerated the evolution of single sign-on (SSO) solutions with two-factor authentication and multi-factor authentication. The rapid shift to remote work has led to a huge surge in cyberattacks and credential theft attacks. In fact, since the start of the pandemic, credential theft attacks have risen by 55%.
Over the last two years, CIOs and their organizations have been forced to reevaluate the delivery of their systems, including increased adoption of a hybrid remote model that accelerates their operational, customer experience, and digital transformation strategies while staying safe and secure.
Let's explore the differences and build the case for the right authentication option for your organization.
The increase in remote access has caused a splurge in user accessibility of hundreds of web and mobile applications across multiple devices (laptops, tablets, and smartphones). These apps require specific usernames and passwords, posing threats for credential stuffing due to a lack of strong passwords, re-used passwords, or common passwords used across multiple apps and sites.
That's why CIOs and Security leaders are looking for better ways to implement identity and access management that protects their digital assets while creating a more seamless experience for their consumers with a single sign-on.
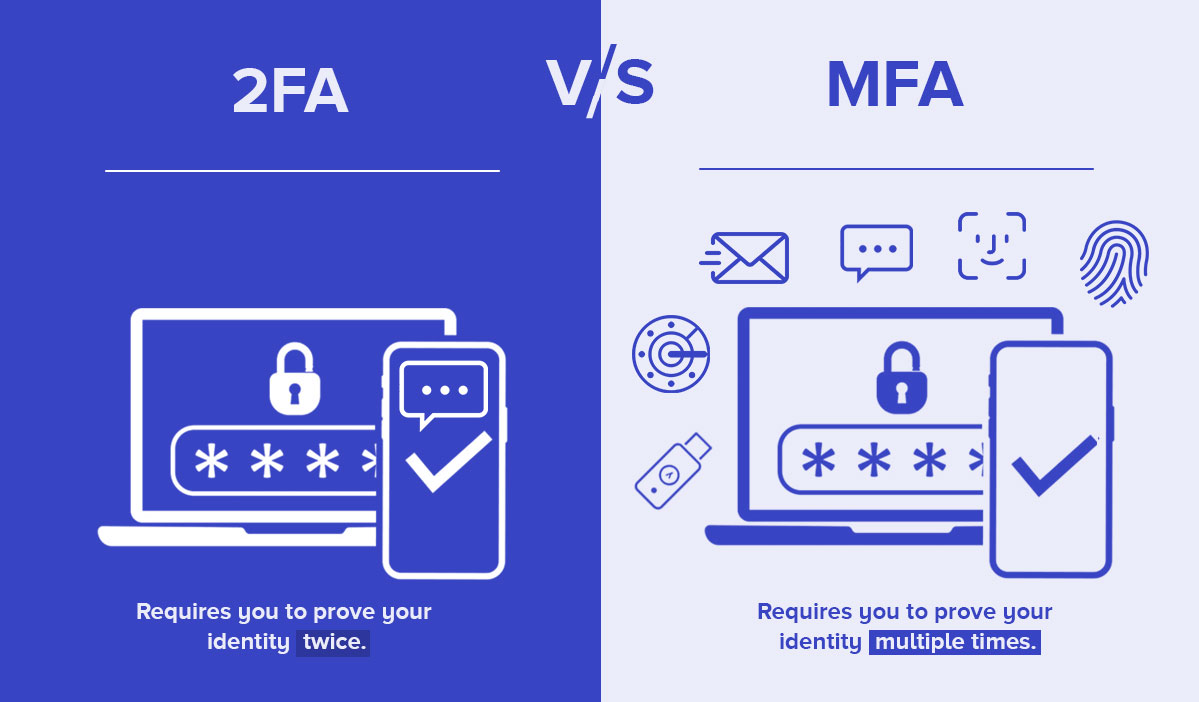
Two-factor authentication (2FA) is the simplest and most effective tool to provide a secure layer of authentication on top of the login credentials. After the users enter their credentials, they need to verify their identity using an independent factor (email, SMS, security questions, social profile, etc.). The use of these protocols restricts suspicious login attempts to access the system, even if someone maliciously accesses the consumer's password.
If you are a CIO or security leader looking to meet compliance requirements and develop a robust multi-layered access environment across users, devices, cloud, and on-premise applications, MFA is your best choice. MFA is an authentication system that requires a user to provide more than two forms of identity verification before allowing access to a network or application.
Most MFA authentication is based on three types of additional information. The list below reviews these authentication methods used to secure systems.
The main difference between 2FA and MFA is the number of credentials used to access an account. SSO is all about users gaining access to their resources with a single sign-on authentication. Two-factor authentication uses just two of these methods to verify and authorize a user's login attempts, whereas MFA uses two or more of these checkpoints. This makes for the argument that MFA is stronger than 2FA, though both are easy to implement.
Singe factor authentication is the most common security process that requires something you "know," such as a password. An excellent example of this is when you enter a password to log in to your Gmail account to access your email. Unfortunately, passwords are not secure anymore. Cybercriminals have derived methods to intercept somebody's password via keylogging, phishing, or rainbow table attacks.
Using a 2FA or MFA solution adds more authentication factors, eliminating the risk associated with weak or stolen passwords. Think of every factor as an additional lock with varying difficulty levels of breaking them.
Bringing an SSO MFA solution like QuickLaunch to your user's login experience can help you block malicious login attempts and the possible risk of password-related breaches. Attackers will not pass through the additional layer of security added by MFA. QuickLaunch provides multiple authentication factors, such as email, SMS, security questions, mobile push, YubiKey, and biometric authentication (voice recognition, fingerprint scanning, or facial recognition).
If attackers crack through your password layer, they have to steal remote access to your phone, email, biometric, and mobile to log in to your account, which isn't impossible.
Nobody's perfect. It's human to err. Sometimes you work under stress or pressure, and it's so easy to get distracted. Attackers know this, trying to attack you when you are the weakest. You can make a mistake that will cost you your data and money. Two-Factor authentication significantly mitigates the probability of human error but does not eliminate it. Introducing yet another authentication factor will make your authentication even stronger and chances of human error negligible. Here is when MFA comes to action.

To reiterate, MFA involves introducing more authentication factors to the process of authentication. Two-factor is a subset of MFA that uses precisely two credential factors. Using just one factor in the form of a password is not secure enough, and that's why you must enable MFA in your organization.
Time is of the essence. Now that you understand the Difference between 2FA and MFA and understand the risks of using single-factor passwords to access your company systems, improving security should be your number one priority to protect your organization.