Identity Lifecycle
Management (ILM)
QuickLaunch Identity Lifecycle Management automates the user identity journey—from onboarding to offboarding. Connect HR, SIS and directory systems to dynamically provision accounts, assign entitlements and revoke access—ensuring secure, policy-aligned access across the entire lifecycle
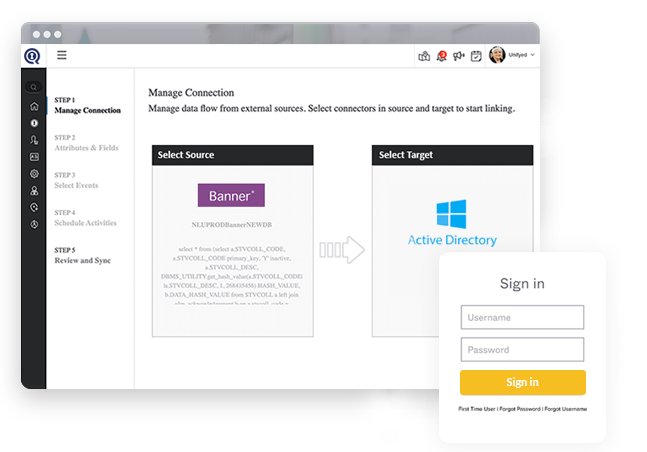
Securely automate user provisioning, deprovisioning and access assignment—at enterprise scale.

Experience seamless operations with automated access control.
QuickLaunch empowers IT teams to streamline identity security, compliance and lifecycle management across both cloud and on-premises systems. Automated directory provisioning and access controls streamline onboarding and offboarding, eliminating errors and manual effort. Role-based provisioning, including dynamic and static role assignments, simplifies account provisioning , while time-bound access ensures credentials are revoked when no longer needed. Orphaned accounts are automatically detected and deprovisioned, helping prevent both risk and unnecessary license expenditures. Built with a user-friendly configuration interface, QuickLaunch enables IT teams to effectively manage identities securely and efficiently—without the overhead.
Identity Lifecycle Management Features
Prebuilt Connectors
QuickLaunch provides a comprehensive library of prebuilt connectors for Higher Ed focused systems like Banner, Jenzabar, Workday, ADP and Office 365. These connectors enable seamless provisioning, bi-directional synchronization, and reconciliation across diverse IT ecosystems—no custom code required.
Automated Provisioning
Create user accounts and assign appropriate entitlements automatically when the user appears in source systems, such as SIS (Banner, Jenzabar), HRIS platforms (Workday, ADP), or Identity Stores (LDAP, AD). Provisioning is immediate, ensuring users have access from day one.
Automated Deprovisioning
When users leave - whether due to graduation, transfer, or termination—QuickLaunch automatically revokes access across all connected systems. This reduces risk by eliminating orphaned accounts and enforcing least-privilege security access by default.
Role-Based Access Control (RBAC)
Grant access based on defined roles, ensuring that access is appropriate to their role (e.g., student, adjunct, staff). RBAC policies are centrally managed and dynamically enforced as user attributes or roles change.
Birthright Provisioning
Automatically assign baseline access and entitlements to new users based on their role. Students, faculty and staff get the right entitlements immediately —without manual IT involvement.

Dynamic Group Management
Automatically assign users to groups based on profile-based rules (department, course enrollment, job title or location). These group control access to downstream app access and resources.
Access Reporting & Analytics
Track user entitlements, including how and when they were granted. Visual dashboards and exportable reports help IT and compliance teams to monitor access trends, lifecycle events and provisioning outcomes.
No-Code Configuration
Deploy and manage ILM solutions quickly using a no-code configuration wizard. Admins can configure workflows, mappings and business rules without needing custom scripts or third-party tools.
Empowering institutions through strategic partnerships