7 Features to Look for while Choosing a Multi-Factor Authentication (MFA) Software
March 22, 2022
How Identity and Access Management Shields Your Higher Education Institution in 4 Steps
April 13, 2022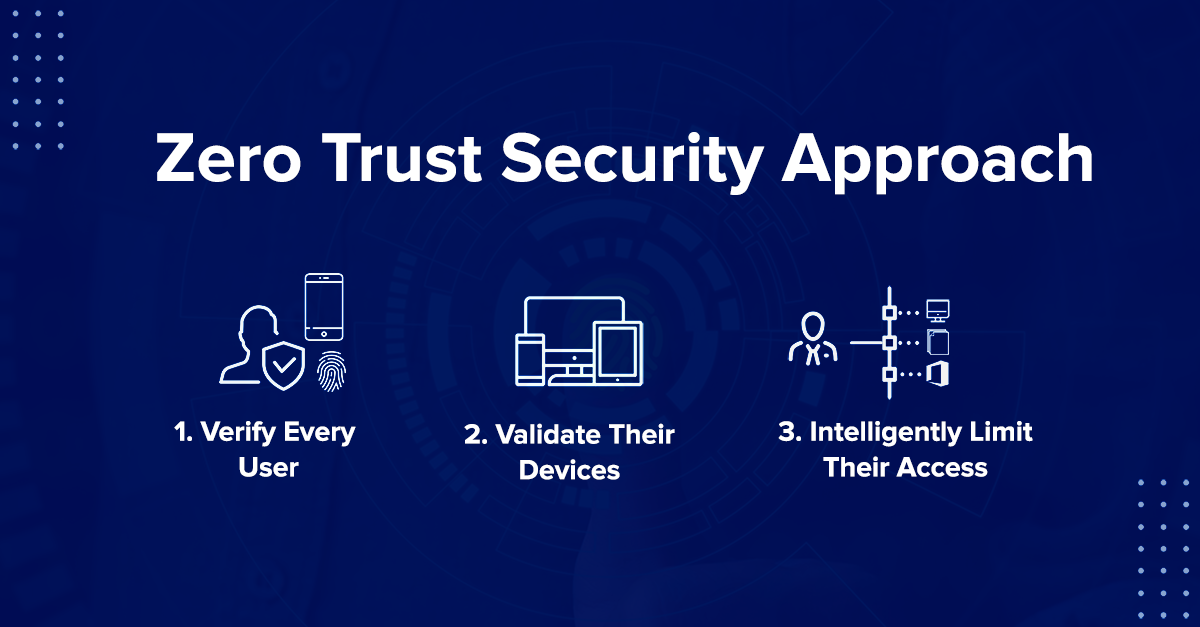
The adoption of cloud and mobile means that a business no longer has a network perimeter-centric view of security. Instead, it securely needs to enable access for various users (employees, partners, students, etc.) - regardless of their device, location, or network.
With many businesses offering work-from-home to employees post COVID-19, accessing applications from multiple devices outside the business circumference is not uncommon. These new business settings have increased the risk exposure. The “Trust but verify” approach is no longer an option.
The “Trust but verify” model means if a user has correct credentials, they are admitted to any app, site, or device they have privileges for. It results in increasing risk exposure, thawing what was once trusted by a business zone of control, and leaving many organizations prone to data breaches, ransomware attacks, and malware.
Modern-day organizations need a new security model that effectively adapts to a complex environment embraces the hybrid workplace, and secures devices, apps, data, and people, wherever they are located.
The U.S. Executive Order on Cybersecurity delivers a valuable guidance to make the world safer for everyone. To be secure and competitive, enterprises need a zero-trust security approach to protect enterprise data, wherever the users and devices are, while ensuring that applications work seamlessly.
What is ZERO TRUST?
The Zero Trust security model assumes a breach and verifies every request as though it initiates from an open network. Regardless of where the request originates or what resources are accessed, the Zero Trust approach teaches us never to trust, always verify.
This model ensures that the right people have access to the essential resources in the right context and that access is assessed continuously by the users frictionlessly. But this doesn’t happen overnight.
The Principles of Zero Trust Security
Achieving Zero Trust security can be challenging for many organizations, but most of them leverage identity and access management (IAM) to start their Zero Trust journeys. As organizations implement Zero Trust architecture, they progress through different stages of IAM maturity. These stages are:
1. Constant Monitoring and Validation
The Zero Trust network philosophy assumes that attackers reside both within and outside the network, so no machines/users should be automatically trusted. Zero Trust will verify user identity and privileges and the device identity and security. The logins, connections time-out, and devices will be re-verified again and again.
2. Least Privilege
One of the essential principles of Zero Trust security is least privilege access. It means giving users only as much access as they need. This will minimize users' exposure to critical areas of the network. It is implementing the least privilege involves sensibly managing users' permissions.
3. Device Access Control
Zero Trust also requires firm controls on device access in addition to controls on user access. The Zero Trust system monitors how many unique devices are trying to access an organization's network, ensures every device is authorized, and assesses all the devices to ensure they are not compromised. It minimizes the attack surface of the network.
4. Micro-Segmentation
Micro-Segmentation is done to break security perimeters into smaller zones for maintaining separate access for different parts of the network. Zero Trust leverages micro-segmentation to ensure that a user with access to one of those zones cannot access any other zone without separate authorization.
5. Prevent Lateral Movement
When an attacker gains access to a network while moving within the network, it is called lateral movement. These movements can be difficult to detect even if the attacker's entry point is discovered because the attacker might have entered other parts of the network.
Zero Trust models are designed to prevent attackers from moving laterally within a network. Zero Trust architecture is segmented and gets re-established periodically; an attacker cannot migrate to microsegments within a network.
This makes it easier to detect the attacker's presence and quarantine the compromised device or cutoff further access.
6. Multi-Factor Authentication
MFA (Multi-Factor Authentication) is the golden bullet of the Zero Trust Security gun. It is an umbrella term for verifying the identity of end-users with a password and at least one other way of authentication. The other way of authenticating can be through email, SMS, phone, mobile push, hardware tokens, authenticator apps, biometrics, or other means. MFA ensures that the user accounts stay secure even if the credentials are compromised.
The Bottom Line
As IT and cybersecurity professionals, we like the idea of Zero Trust. Any user will have limited access and privileges to the applications, devices, or other resources based on a fixed hierarchy. But putting the Zero Trust model into practice isn't that simple. By starting identity as the foundation of your enterprise, you can tackle the key security challenges and take your organization towards the road of Zero Trust.