Zero Trust: An Evolution or Demise

Fall Semester Readiness: A Guide for Upgrading IT Infrastructure in Higher Education Institutions
July 23, 2024
Is Passwordless Authentication the Future?
August 22, 2024
In an era where data breaches and cyber threats have become almost commonplace, the concept of Zero Trust has emerged as a beacon of hope in the realm of cybersecurity. Zero Trust, often touted as the future of network security, challenges the traditional perimeter-based approach and adopts a more proactive and cautious stance. But as technology continues to evolve, the question arises: Will Zero Trust evolve along with it, or will it become obsolete?
The Birth of Zero Trust
Zero Trust was introduced by Forrester Research in 2010, and its core principle is simple yet revolutionary: "Never trust, always verify." It advocates for the idea that trust should not be automatically granted to any user or device, even if they are inside the corporate network. Instead, verification and authentication should be continuous and context-aware, allowing access based on the user's identity, the device's security posture, and other relevant factors.
Key Findings from Gartner Report- 2023 Strategic Roadmap for Zero Trust Security Program Implementation
- Organizations in North America, and increasingly other regions, have a strong desire to adopt a zero-trust security paradigm to reduce risk to their organization, but have difficulty translating this desire into an actionable strategy with a roadmap, projects and measurable outcomes.
- Vendors are marketing “zero trust” heavily as a way to buy improved security for organizations, but zero trust is not a technology. A zero trust paradigm regroups and emphasizes a set of cybersecurity principles that can be implemented across a range of technologies to address specific risks to an organization.
- Organizations that implement technologies without a clear strategy and careful planning waste time and resources on incomplete implementations, and potentially create a false sense of security. Common roadblocks include legacy technology, scalability, integration and capability gaps in zero trust technology implementations, organizational resistance, and failure to consider business process impact.
- Zero trust technology implementations introduce significant operational overheads, particularly when organizations lack a formal definition of “who should have access to what” and do not integrate technical controls that adapt to a dynamic environment.
The Zero Trust Framework
Zero Trust operates on a set of guiding principles:
1. Verify Identity: Ensure that the identity of users and devices is authenticated before granting access.
2. Least Privilege Access: Only provide access to the resources and data necessary for a user's role or task.
3. Micro-Segmentation: Divide the network into smaller, isolated segments to limit lateral movement in case of a breach.
4. Continuous Monitoring: Monitor network traffic, user behavior, and device health in real-time to detect and respond to threats promptly.
5. Explicit Access Control: Specify and enforce access policies for every user and device, leaving nothing to chance.
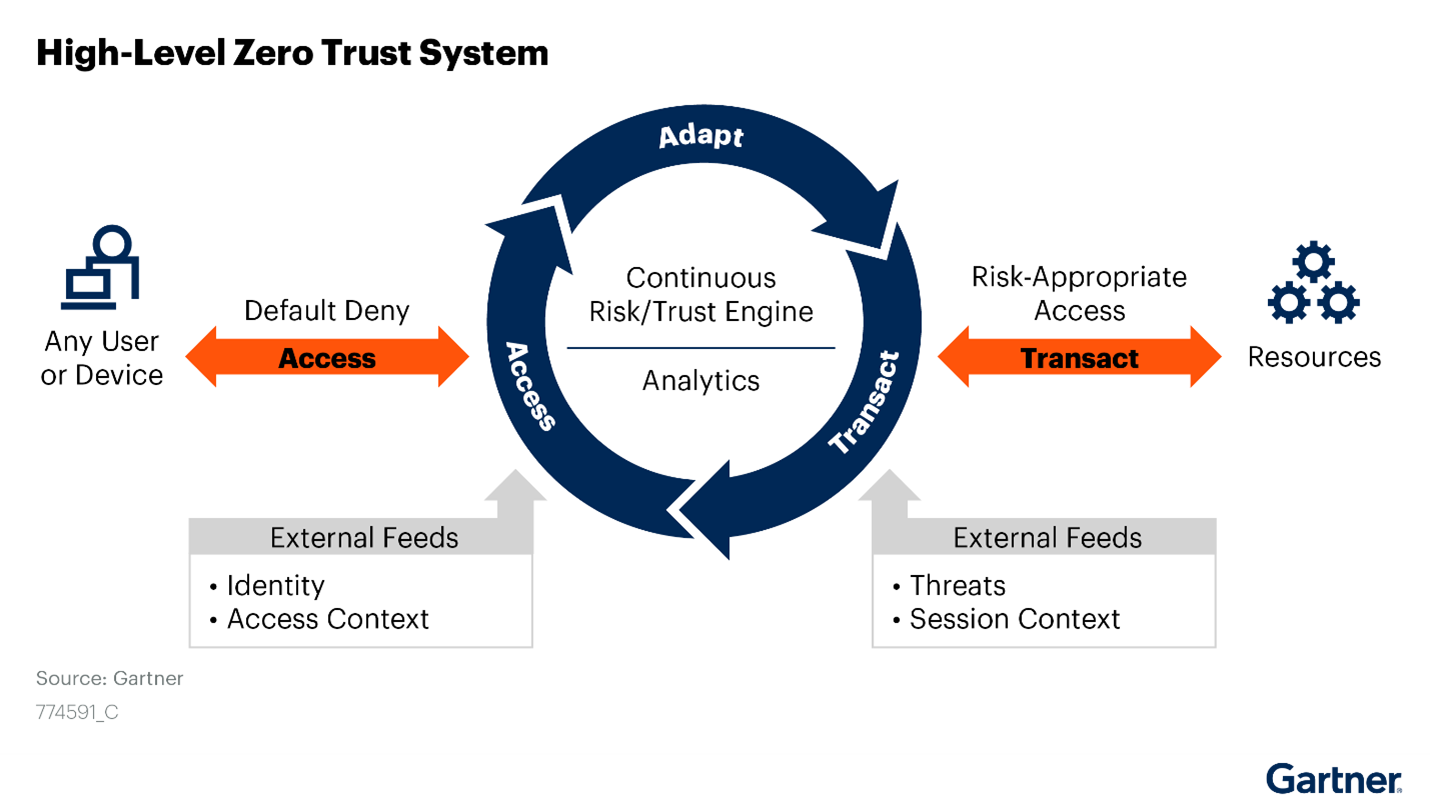
The Challenges Zero Trust Addresses
Zero Trust was born out of the need to address several critical challenges in cybersecurity:
1. Perimeter-Based Security Is Insufficient: Traditional security models, relying on perimeter defenses, have proven ineffective against advanced threats and insider attacks.
2. Proliferation of Remote Work: The rise of remote work has expanded the attack surface, making it necessary to secure access from anywhere.
3. Insider Threats: Insider threats, intentional or unintentional, continue to pose a significant risk to organizations.
4. Evolving Attack Vectors: Cybercriminals are constantly devising new attack vectors and techniques to breach networks and steal data.
5. Compliance and Data Protection: Regulatory requirements demand more rigorous data protection measures, making Zero Trust a strategic choice for compliance.
The Evolution of Zero Trust
The journey of Zero Trust has just begun, and its future is promising:
1. Integration with AI and Machine Learning: Zero Trust is evolving to incorporate AI and machine learning for more intelligent and adaptive threat detection. These technologies can analyze vast amounts of data to identify anomalies and patterns that may be indicative of a breach.
2. User Experience Improvements: As Zero Trust matures, efforts are being made to ensure that it doesn't hinder user productivity. Solutions are becoming more user-friendly, allowing for seamless authentication and access while maintaining security.
3. Zero Trust Beyond Networks: Zero Trust is expanding its reach beyond network security to encompass cloud resources, applications, and endpoints. This evolution reflects the reality of modern IT environments, which are increasingly decentralized.
4. Continuous Authentication: Traditional authentication methods like passwords are increasingly being replaced by continuous authentication methods, such as biometrics and behavioral analytics, to enhance security.
5. Zero Trust as a Framework: Zero Trust is transitioning from a buzzword to a comprehensive security framework. Organizations are adopting it not as a product but as a holistic strategy to safeguard their digital assets.
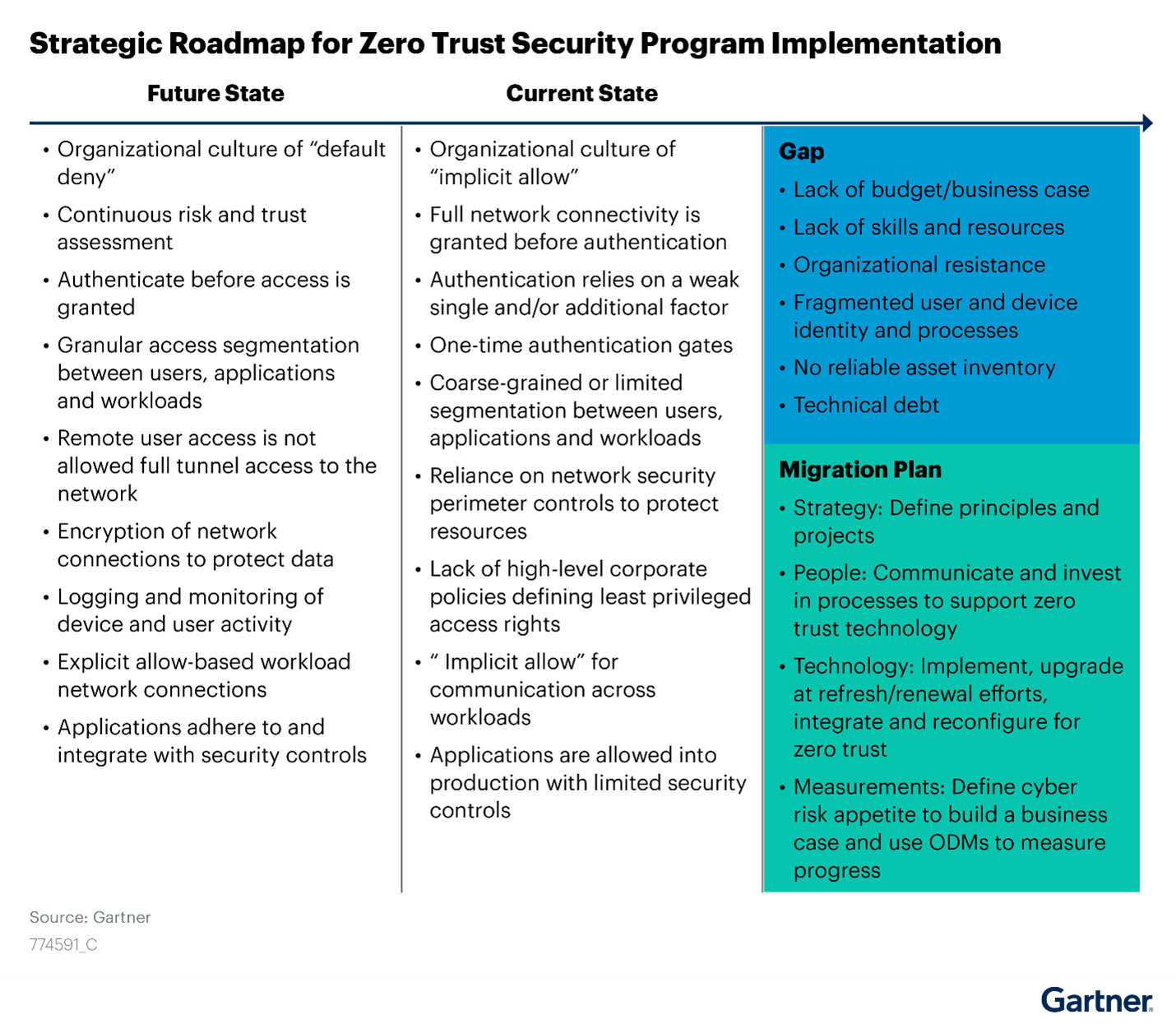
The Fate of Zero Trust
So, Is Zero Trust: An Evolution or Demise? The answer lies in its adaptability. As long as it continues to evolve alongside emerging threats and technological advancements, it will remain a potent tool in the cybersecurity arsenal. Zero Trust's ability to address current challenges, integrate cutting-edge technologies, and offer a comprehensive security framework positions it to thrive in an ever-changing digital landscape.
In conclusion, Zero Trust is not a static concept; it's a dynamic and evolving approach to cybersecurity. Its continued relevance and effectiveness depend on its ability to adapt, learn, and stay ahead of the evolving threat landscape. As long as the principles of "never trust, always verify" remain at its core, Zero Trust is likely to evolve and remain a cornerstone of modern cybersecurity strategies.
QuickLaunch, a leading identity and access management (IAM) solutions provider, plays a crucial role in helping organizations align with Zero Trust principles. With its robust suite of IAM tools, QuickLaunch empowers organizations to "Verify Identity" through multi-factor authentication, enforce "Least Privilege Access" with role-based permissions, and implement "Continuous Monitoring" of user activities for real-time threat detection. Leveraging artificial intelligence and machine learning, QuickLaunch enhances threat detection and adapts to evolving risks, while simultaneously prioritizing a seamless "User Experience." As organizations embrace Zero Trust beyond networks, QuickLaunch's IAM capabilities extend to securing access to cloud resources, applications, and endpoints. In this ever-evolving landscape of cybersecurity, QuickLaunch's adaptable IAM solutions provide a critical foundation for organizations aiming to implement and maintain a Zero Trust security model.
Want to try? Schedule a free demo here.




