Get SSO Software That Supports Multiple Applications Out-of-the-box
December 14, 2017The Problem
The IT Consumerization wave brought into our work lives, a plethora of apps such as email, productivity suites (such as G-suite), Apps (such as Evernote, Box etc.), CRM tools, ERP tools, HRMs and 1000s of other such applications.
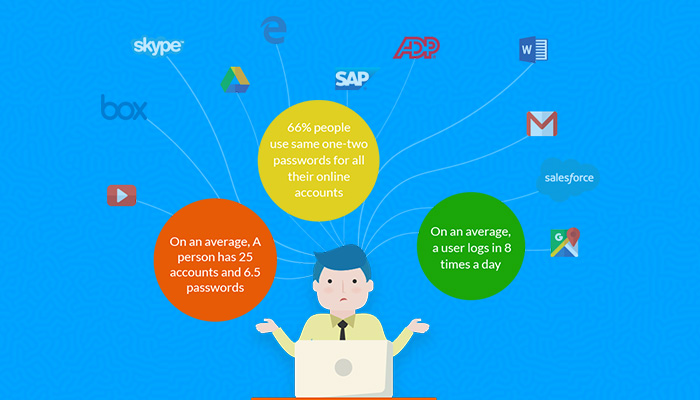
This has also brought along with it, a flurry of usernames and passwords thereby leaving the end-user completely at sea. How do you effectively manage and use these applications since the lifeline of your business depends heavily on these tools? How do you avoid getting into this relentless cycle of forgetting and resetting a dozen passwords a day? Single Sign-On is something you should seriously consider.
What is "Single Sign-On"?
Single Sign-On (also known as SSO) helps a user gain access to multiple applications through an authentication process that uses just a single set of credentials. It enables single-click access to a whole lot of applications thereby mitigating the need to remember an endless list of usernames and passwords. It not only shortens the time to get started with these apps with just a click of single button but also has a whole lot of security benefits from an organizational standpoint.
- SSO allows the user to log in and access multiple applications without logging separately to each one.
- SSO is a user authentication mechanism that enables 1-click access to unlimited number of applications
- SSO enables IT teams monitor user accounts providing admin control.
How does Single Sign-On work?
The Single Sign-On service authenticates the end user for the multiple applications that the user has access to and eliminates any further triggers when the user switches to different applications in the same session.
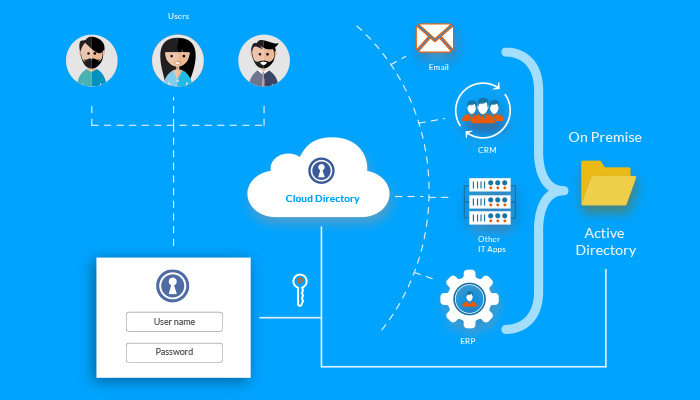
There are 3 basic elements that constitute the Single Sign-On mechanism namely, the central Server, the Applications, the cookie. Applications place their trust on a Central Server and each time a user tries to login, a cookie is set on the Central Server. At subsequent attempts to login to other applications, the set cookie comes into play thereby avoiding the need for authentication one additional time, redirecting the user to the application he/she intends to use. This chain reaction continues until the Application is configured to trust the Central Server.
SSO in Higher-Education
- Increases Portal adoption among students
- Seamless user experience for students
- Flexibility for teachers to use apps of their choice
- Cuts Helpdesk load related to password queries
SSO in HealthCare
- Helps in better compliance such as HIPAA etc.
- Secures sensitive patient-related information
- Prevents unauthorized access to sensitive data
- Enables role-based authentication
SSO in Hospitality
- Enables role-based user profiling
- Better Account management for guests to access internet etc.
- Enables having a customizable dashboard giving 1-click access
- Puts security & compliance on autopilot mode
- SSO in Retail
- Better & safe access to payment gateways
- Better interconnection with sister portals
- Seamless vendor management using SSO
- Bridges gap between e-retail & brick-and-mortar
LET’S TALK TECH!
SSO and SAML:
Security Assertion Markup Language is a protocol that Single Sign-On uses. Security Assertion Markup Language (SAML) is an XML standard for exchanging single sign-on information between an identity provider (IdP) which asserts the user identity and a service provider (SP) who consumes the user identity information.
Google’s logging in procedure where logging into Google account automatically logs you into other Google applications such as Google Plus, Google Maps, Gmail and YouTube is a brilliant example of Single Sign-On.
Where’s my SSO?
On-Premise:
On-Premise Single Sign-On requires high cost of personnel to deploy the system along with long hours spent on troubleshooting and debugging applications.
Cloud:
Cloud Identity and Access Management services let you login once to access all the services making it convenient for IT to give permission to end users to access cloud services.
Hybrid:
Hybrid Single Sign-On uses one directory (whether it's AD or cloud-based Google directory) for one half of the organization and Cloud directory for the other half. This lessens the change made in the directory and gives space to the IT management.
Some open source Single Sign-On solutions
Josso
JOSSO is an open source identity and access management solution focused on streamlining implementations through a visual modeling and generative approach. Founded in 2004, it is used by around 4,000 organizations worldwide.
Keycloak
Keycloak is an open source Identity and Access Management solution aimed at modern applications and services. It makes it easy to secure applications and services with little to no code.
Gluu
The Gluu Server is free open source software and can be deployed in production for free! The Gluu Server can be configured to achieve single sign-on to any SAML 2.0 or OpenID Connect protected application.
OpenAM
OpenAM is an open source access management, entitlements and federation server platform. It is sponsored by ForgeRock. OpenAM originated as OpenSSO, an access management system created by Sun Microsystems and now owned by Oracle Corporation. OpenAM is a fork which was initiated following Oracle's purchase of Sun.
A word of Caution:
An Open Source Single sign-on may not have a promising product lifecycle and even though it’s free, the custom configuration and deploitation are not. Also, when it comes to Troubleshooting, you are on your own.