Ensuring the right people have the right access to the right systems and applications is at the heart of identity and access management. Organizations across the globe have different roles to manage at the time of onboarding. This potential organizational streamlining can be achieved with a solid role-based access control (RBAC) policies.
Modern-day organizations understand the value of a systematic approach to maintain defined roles in organizational hierarchy. They understand that not every job description will have its own role but condensing 80% of job-related privileges into roles significantly improving the ability to manage access.
Administrators identify roles, grant permissions and maintain the security systems.
Workers are grouped together based on the tasks they perform.

Permissions outline what people can and cannot do.
Why Role-Based Access Control?
Streamline access control by reviewing roles
Onboard users faster by automatically assigning access based on attributes
Automatically remove accesses associated with old roles
Roles vs Groups: The Difference
There is an apparent similarity between roles and traditional groups. A group is a collection of users, rather than a collection of permissions, and permissions can be associated with both users and the groups to which they belong. The ability to tie permissions directly to users in a group-based mechanism can be regarded as a "loophole" that makes it difficult to control user-permission relationships.
RBAC requires all access through roles, and permissions are connected only to roles, not directly to users. Another aspect of RBAC that distinguishes it from traditional group mechanisms is the concept of a session, which allows activation of a subset of roles assigned to a user.
Defining the Roles
Roles dictate authorization within an RBAC system. It is important to define roles properly, otherwise, large groups of people within an organization / institution can’t do their work. Roles can be defined by these elements:
1. Credibility
Top-level management will have access to a few files that interns or newly onboarded users can never see.
2. Responsibility
Top-level management and their immediate subordinates may hold similar powers within an organization but different core functions.
3. Skills
A skilled worker can be trusted to work within sensitive documents without errors while a novice can make tragic mistakes. So, it becomes important to grant access accordingly.
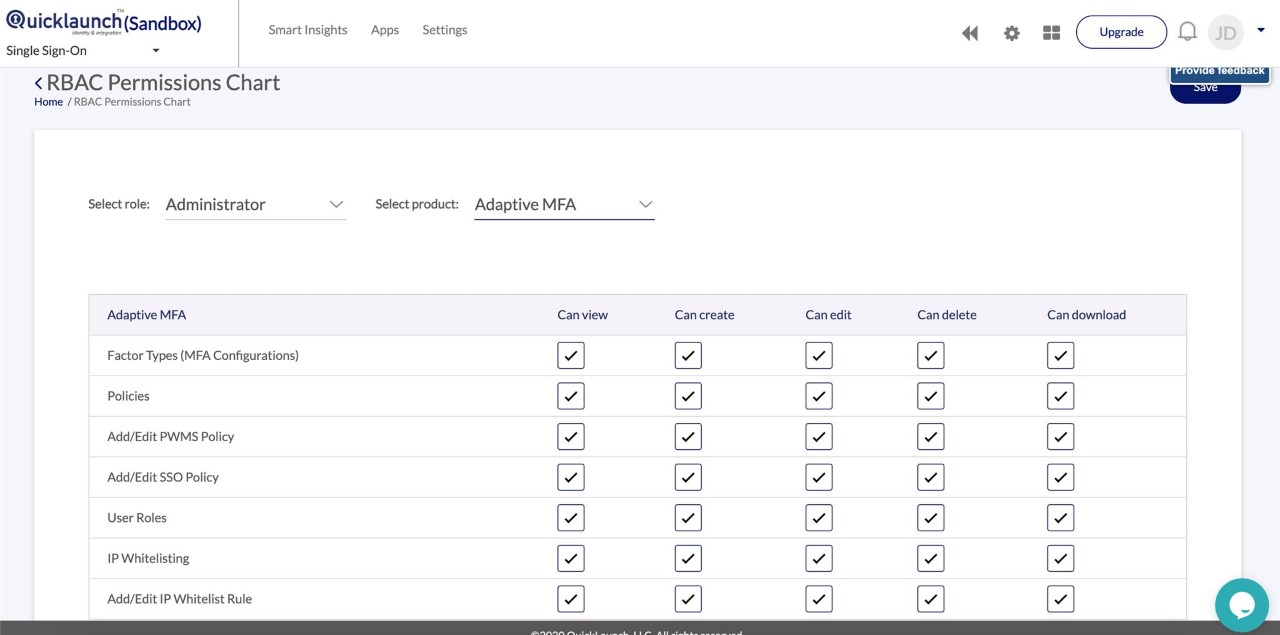
Supported Role-Based Access Control Permissions
1. View: A user having access to a file can only scan through it without making any changes to it.
2. Create: A user have access to create a new file at a specified location.
3. Edit: A user can edit a file which he/she might not have created.
4. Delete: A user have permissions to delete a file which he/she might not have created.
5. Download: A user have the permission to download a file and send it as an email attachment.
Global Administration and Control
Change/revoke access for many users all at once by changing permissions associated with a certain role.
Smooth & Swift Onboarding Experience
As people join, change positions, or move within your institution / organization, you don’t have to worry about individual permissions as roles will take care of everything.
Reduce Complexity
Newly onboarded users gain access to the systems/applications based on their roles not on long lists of server or document requirements. This ease out creating, maintaining, and auditing policies.
No More Blunders
Adding permissions for different individuals gives you plenty of options to make mistakes. Just change a role’s access, and you are less likely to grant wrong permissions to someone.
Save Time and Money
When administrators’ duties shrink, organizations save on security administration, saving time and money.
Ready to Implement Our RBAC-Powered Solution?
It might feel intimidating to implement a solution like this, but this implementation can be smoother and manageable with a little assistance. Try QuickLaunch to simplify processes at your institution / organization and take control of digital identities.
