6 Things to Do To Keep Your Users, Data & Apps Safe – World Password Day Special #LAYERITUP
May 3, 2018
On-premises SSO: A Costly Affair or Worth Spending?
November 17, 2018Every organization no matter which industry domain it belongs to or what size it holds, there is always a need of order and security to operate efficiently. Also, the primary concern of every organization is dealing with people, contractors, employees, students, partners, customers and so on. Identity management is a field of information technology which is all about order and security with respect to managing people. Identity management technologies automate business processes which start with password management, automation of security reviews, risk management assessments and audits.
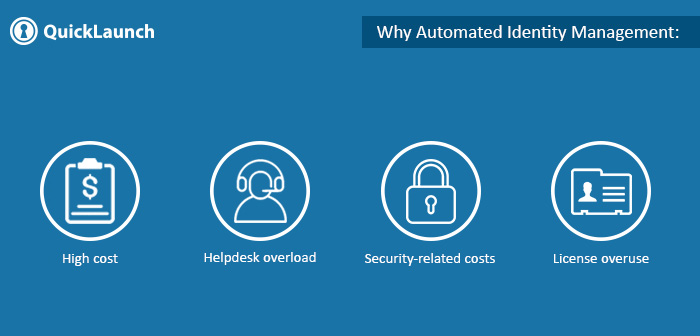
Why Automated Identity Management:
Managing identities is both time and money consuming. The enterprises need to understand that, to bring new products and market them quickly, they need to keep the cost down and stay competitive.
High cost: The manual identity management cost is huge. This cost includes the cost of IT staff which creates and maintains users accounts, roles, and access privileges.
Helpdesk overload: While looking for enterprise helpdesk usage statistics, it is visible that identity-related issues cause a huge impact on helpdesk load. This is another reason why automated identity management workflow can be of real value.
Security-related costs: Although security incidents are relatively rare, yet there is a significant cost involved even in minor incidents. Security-related investigations and suspicious activities. Deprovisioning is another problem which creates a security risk, therefore, accounts which are created must be deleted.
License overuse: Users in every organization look for as many access rights as they can get, no matter if he needs it or not. This makes sense also, since in an organization where any access request takes a lot of time. But again, this invites to a problem since all the information systems are full of accounts which are never used. This shows that there is a waste of money as many software products have user-based licensed. The organization pays for license and support costs which never was used.
There are other reasons also associated with manual identity provisioning, but high cost is a substantial reason for switching to automated identity management. Let’ see how identity provisioning can be beneficial for enterprises.
Provisioning and De-provisioning in Higher-ed:
Unlike retail and other commercial ecosystems, in the educational domain, universities and colleges face distinct identity and access challenges. Just like financial services and retail are viewed at higher-risk from a cybersecurity and governance point of view, the higher-education is just as critical.
According to the Privacy Rights Clearing House higher education “accounts for 17 percent of all reported data breaches, ranking second only to the medical industry,”.
Educational Institutions, universities, and colleges handle a tremendous amount of sensitive data. This personal information comprises of contact information of student, staff, and faculty. Also, there is financial and credit data pertaining to them. Furthermore, even there is protected health information which organization encloses within. With such protected information and confidential data, institutions need to adhere to compliance requirements. Along with this, there are many challenges that universities and colleges face.
With ever-changing populations (students' admissions, enrollments, and de-commissioning), complex non-hierarchical structures and overlapping roles and identity sources, the colleges and universities face varied challenges that a standard identity management solution simply can’t address. Identity Access Management Framework mitigates uniquely the challenges which colleges and universities faces. With a mission to help institutions in minimalizing their challenges, IDAM solution offers complete security, data privacy and governance, and adaptability.
Major Challenges Universities and Colleges faces:
1. Users with Multiple Roles and Access Levels
Unlike other commercial institutions, universities have multiple roles for single identity, whereby often seen that students may also work as staff, faculty may also be enrolled as students, and faculty and graduate students are often also alumni.
Your users are always expected and tasked with remembering and managing multiple user credentials for their educational and work activities. This leads to another bothersome task where assistance is required in resetting forgotten passwords or dealing with user experience issues.
You may experience increased support calls which creates a heavy burden on a help desk. Also, there could be a chance you may encounter data sync problems due to multiple accounts including users getting incorrect permissions that need to be fixed. All this results in overburdened help desk staff.
2. Using technology without compromising security
Today college students use technology on daily basis and view it as an essential tool. For completing the variety of tasks like research work, completing coursework and finishing off with assignments, students want to unleash the power of technology.
Students look forward to their school’s technology which could easily integrate seamlessly into their lives and simplifies their learning experience. Updated hardware and software solution are the least which an average college student, a budding engineer and a technology genius expect their college to provide. Here comes the challenge for colleges, to provide consistent and usable technology which students can expect without compromising their security.
For colleges and educational institutions, the IDAM challenges don’t stop on registration day. The technology is widely used in classrooms as a great learning tool which comes in form of digital content, online file sharing and management solutions and of course collaborative tools. A commonplace as an access for all the associated entities in the higher-education ecosystem without negotiating on security perspective is something which colleges look upon.
3. Ad-hoc workflows and requests
There are chances when visiting faculties and students require network and access privileges while they are at your school or colleges but of course at different levels. Often it happens that burden falls on your staff to create new types of user accounts and IDs which are on the fly. Many times, you are informed on the last minute of arrival which itself is a lot annoying and troublesome.
Although you may be getting this information as requests via paper forms or email chains or in-person account requests but do not forget that this is itself a cumbersome and time-consuming task.
Your staff has already pre-occupied with other relevant and daily university tasks on their plates. Providing and revoking custom network, application and building access to thousands of campus visitors every semester is like sufficing to the needs which are uninvited. This also brings in picture delays, errors and potential compliance and security vulnerabilities which are inevitable.
IDAM benefits for Universities and Colleges:
1. Comprehensive Identity Governance
When a question arises of your students’, faculty members and staff’s identity and personal information access, it becomes a mandate to safeguard their utmost confidential information within college or university secured framework. IDAM framework within which it implements the provisioning and de-provisioning procedures, colleges and universities can expect streamlined identity governance.
IDAM ensures proper identity and access controls are maintained and updated as per your institutional policies, classifications, and personnel changes. With policy driven configurations orphan and rogue accounts automatically gets identified and such accounts get easily enabled for remediation.
With automated de-provisioning, we are implementing the process where the possibility of human error is completely out of the picture. When any of the outside faculty or student is removed from Active Directory they are automatically de-provisioned from all the other connected accounts. We are preventing, in fact effectively closing the doors for visitors to access confidential and corporate data. There is nothing left to do for them. It is simple, quick and can be efficiently implemented.
2. Access Management for student's retention
Your institutions hold some valuable assets which none are other than your bright students and torch-bearers faculties. Identity and Access Management solution offers secured control to authorized users and therefore faculties and other designated authorities can view detailed analytical reports for knowing students’ profiles.
With detailed reports and analytics, scholarship governing bodies or student's retention cells can easily retain students or taking a decision on granting or not granting scholarship, keeping in view the performance of the student. IDAM Framework allows, access to various learning management systems and other third-party applications whereby simplifies tracking of students’ visiting to different learning portal.
IDAM gives a detailed roadmap of a student like access to course management, real-time student tracking, viewing discussion forums and developing intervention programs and early orientation programs before they chose the path to success, thereby retaining students.
3. Automated and policy-driven workflows
Identity and Access Management framework simplifies student enrolment process as it creates a secure environment which requires proper authentication and authorization to access certain data or applications. It offers a centralized access login point which eases work for IT to set up restrictions and monitor accounts.
Identity and Access Management also gives prompts if there is a security breach of any protocol. This is utmost important for schools and colleges as their system not only stores personal data related to school but also social security number and addresses. Another privilege IDAM solution offers is the ability to automatically monitor accounts. This explains that your IT professional should not worry about data hacks and your network always remains secure. Your students can work 24/7 and 24/7 automation feature allows them to reset and manage passwords without needing to contact IT. Conclusively, you don’t have to staff the IT desk at all time.
With security protocols and automated accounts monitoring the IDAM solution gives convenient yet secured access to relevant users without breaching security protocols.
4. Student lifecycle management:
IDAM also takes care of the lifecycle management of every student. It automates every aspect of the student lifecycle, right from the beginning with custom self-service registration (onboarding) and throughout the student journey. This happens using rules, policies, workflows, and API’s.
IDAM solution also comprises of pre-integrated apps for provisioning and de-provisioning. The framework able enables extensible integrations with critical higher education apps and learning management systems like Blackboard, and Canvas.
The framework also helps colleges and universities in realizing various ways. With a streamlined approach, it helps universities and colleges IT team to spend less time in administrating and more time in strategizing. By offering customizable dashboard, an interface tailored to each device, and centralized notifications for new apps, password changes, and messages from IT, framework gives a secured yet easily accessible to authenticated users an ecosystem, where they can work cohesively yet independently.
5. Reconciling process or automating tasks:Compounding the challenges mentioned described above there are over pressurized college IT departments. The custom scripts, complexities of account provisioning and de-provisioning, workarounds for multiple roles which are held by individual users, the need of giving access to the variety of learning apps and other classroom tools is too much for IT department to handle. Adding to this user related errors and help-desk workload can increase the risks for yet more mistakes to be made.
Identity and Access Management framework comes with this solution by automating tasks such as account provisioning and configuration. Your IT department professionals will just have to automate as many manuals and lower-value tasks as possible therefore leaving time and manpower for many critical tasks rather than simply setting up accounts.
The key role which IDAM system plays is enabling technology within Universities’ IT department and other relevant verticals thereby adding value proposition to the framework instead of adding another responsibility to the team.