Guiding CTOs Through Shadows: Exposing Password Vulnerabilities in Higher Education

The Threat of Data Laundering in Higher Education Institutions
February 15, 2024
Passwordless Higher Education: An Essential Protection
March 19, 2024
In the rapidly evolving landscape of higher education, where technological advancements and digital transformations are the norm, Chief Technology Officers (CTOs) play a pivotal role in safeguarding the sensitive information of the institution. One of the most pressing challenges they face is the lurking threat of compromised passwords on the dark web. Many CTOs in the higher education sector are grappling with the alarming reality that their users' passwords might be exposed in the hidden corners of the internet. Today, we delve into the intricacies of this predicament and explore the measures that must be taken to ensure the digital security of educational institutions.
The Dark Web's Cryptic Realm: A Breeding Ground for Cyber Threats
The dark web, a secretive realm of the internet that's intentionally hidden from traditional search engines, is notorious for hosting illegal activities, including the sale and trade of stolen data, credentials, and personal information. This clandestine market provides cybercriminals with an ideal platform to exchange sensitive data, including compromised passwords harvested from various sources.
The Password dilemma in Higher Education
Higher education institutions store vast amounts of personal and academic information, making them attractive targets for cyberattacks. Students, professors, and staff use digital platforms for communication, coursework, and administrative tasks. The security of these platforms relies heavily on passwords, making them the primary line of defense against unauthorized access.
However, password security remains a significant challenge. Users often reuse passwords across multiple accounts, which amplifies the potential damage of a single breach. Cybercriminals, exploiting this tendency, infiltrate databases, steal passwords, and then sell or trade them on the dark web. Higher education CTOs must confront the reality that their institution's usernames and passwords might be floating in this cyber underworld, just a few clicks away from malicious actors.
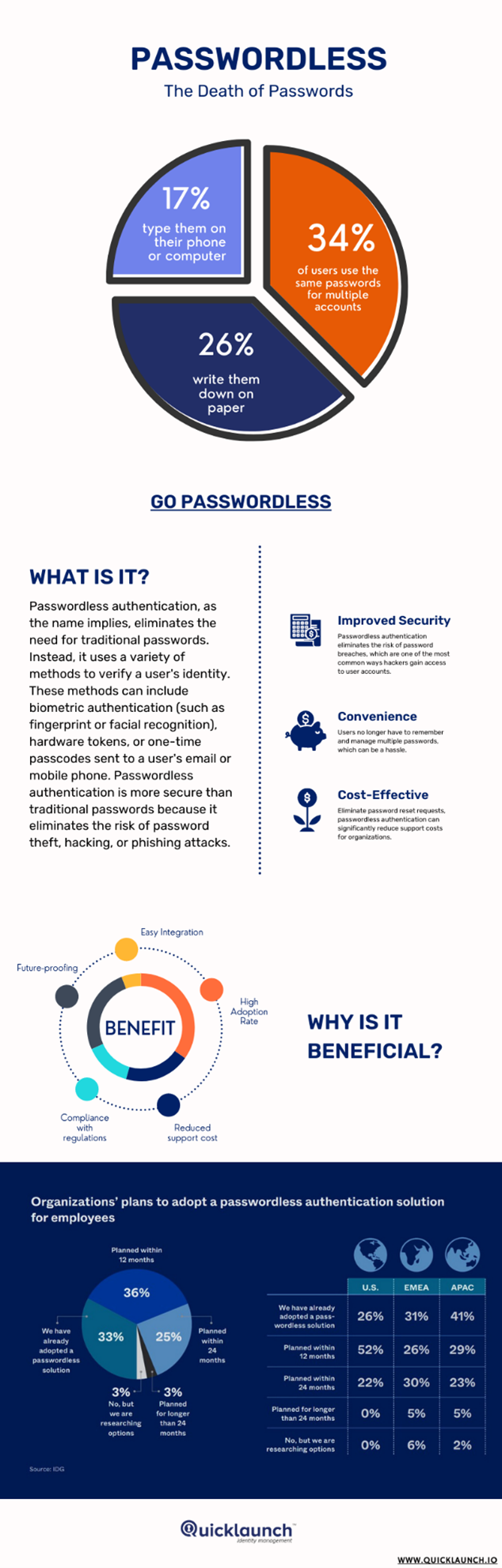
The Implications of Exposed Passwords
The exposure of passwords on the dark web can have dire consequences for higher education institutions. These implications include:
1. Data Breaches and Data Laundering: Compromised passwords can lead to unauthorized access to sensitive student and employee data, resulting in identity theft, fraud, and privacy violations.
2. Educational Disruption: Breaches can disrupt online learning platforms, administrative systems, and communication tools, leading to interruptions in educational activities.
3. Reputation Damage: Security breaches tarnish an institution's reputation, eroding trust among students, parents, faculty, and staff. This can result in enrollment drops and financial losses.
4. Legal and Regulatory Consequences: Data breaches can lead to legal actions and regulatory penalties, especially in light of data protection laws like the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA).
Bolstering Password Security: A Way Forward
To tackle the password security predicament, higher education CTOs should consider implementing the following strategies:
1. Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring users to provide multiple forms of verification before accessing accounts. This significantly reduces the risk of unauthorized access, even if passwords are compromised.
MFA as a Crucial Defense Against Cyber Attacks
The Cybersecurity & Infrastructure Security Agency confirms that Multi Factor authentication (MFA) is significantly more secure than relying solely on passwords. The Canadian government advocates MFA for enhanced cybersecurity against identity theft, credential stuffing, and phishing attacks. This means that organizations and institutions operating in these countries are advised to implement MFA as a critical security measure to protect sensitive data and enhance cybersecurity.
Mandatory MFA for Cyber Insurance - Recognizing the proven effectiveness of MFA, insurance providers are starting to make it mandatory for institutions seeking cyber insurance coverage. By implementing MFA, institutions demonstrate their commitment to robust cybersecurity practices, reducing the likelihood of successful attacks and potential insurance claims. This proactive approach also reflects positively on the underwriting process, potentially leading to more favorable insurance premiums.
2. Regular Security Audits: Conduct comprehensive security audits to identify vulnerabilities and proactively address them. Regular assessments help institutions stay one step ahead of potential threats.
3. Password Management: Encourage users to adopt strong, unique passwords and avoid reusing them across accounts. Password management tools can assist in generating and securely storing complex passwords.
4. Dark Web Monitoring: Collaborate with cybersecurity experts to monitor the dark web for signs of compromised credentials associated with your institution's domain.
5. Cybersecurity Education: Educate students, faculty, and staff about cybersecurity best practices, the risks of password reuse, and the importance of reporting suspicious activities.
6. Passwordless: Get secure and seamless login with multiple passwordless options like Push Notifications, Google Authenticator, Email, SMS OTP, Security Questions, or Preferred Authentication.
All in all, CTOs shoulder the critical task of safeguarding institutions' digital realms. The lurking threats of the dark web continually jeopardize student and staff data security. By maintaining vigilance, implementing strong security measures, and fostering cybersecurity awareness, higher education CTOs can effectively mitigate risks linked to exposed passwords, ensuring campuses remain resilient bastions of learning and innovation.
As cyber risks escalate, safeguarding higher education demands robust cybersecurity. QuickLaunch MFA stands as a proactive defense, streamlining authentication and upholding trust and data integrity. With adaptable authentication and personalized controls, QuickLaunch MFA guarantees precise protection levels, culminating in safer academic spaces. Embracing QuickLaunch MFA is an investment in fortified cybersecurity, bolstering the educational landscape against challenges.




