The Anatomy of a Data Breach: What are They and What to do When You Spot One?
January 19, 2023
What’s the Deal with Authentication Factors?
February 28, 2023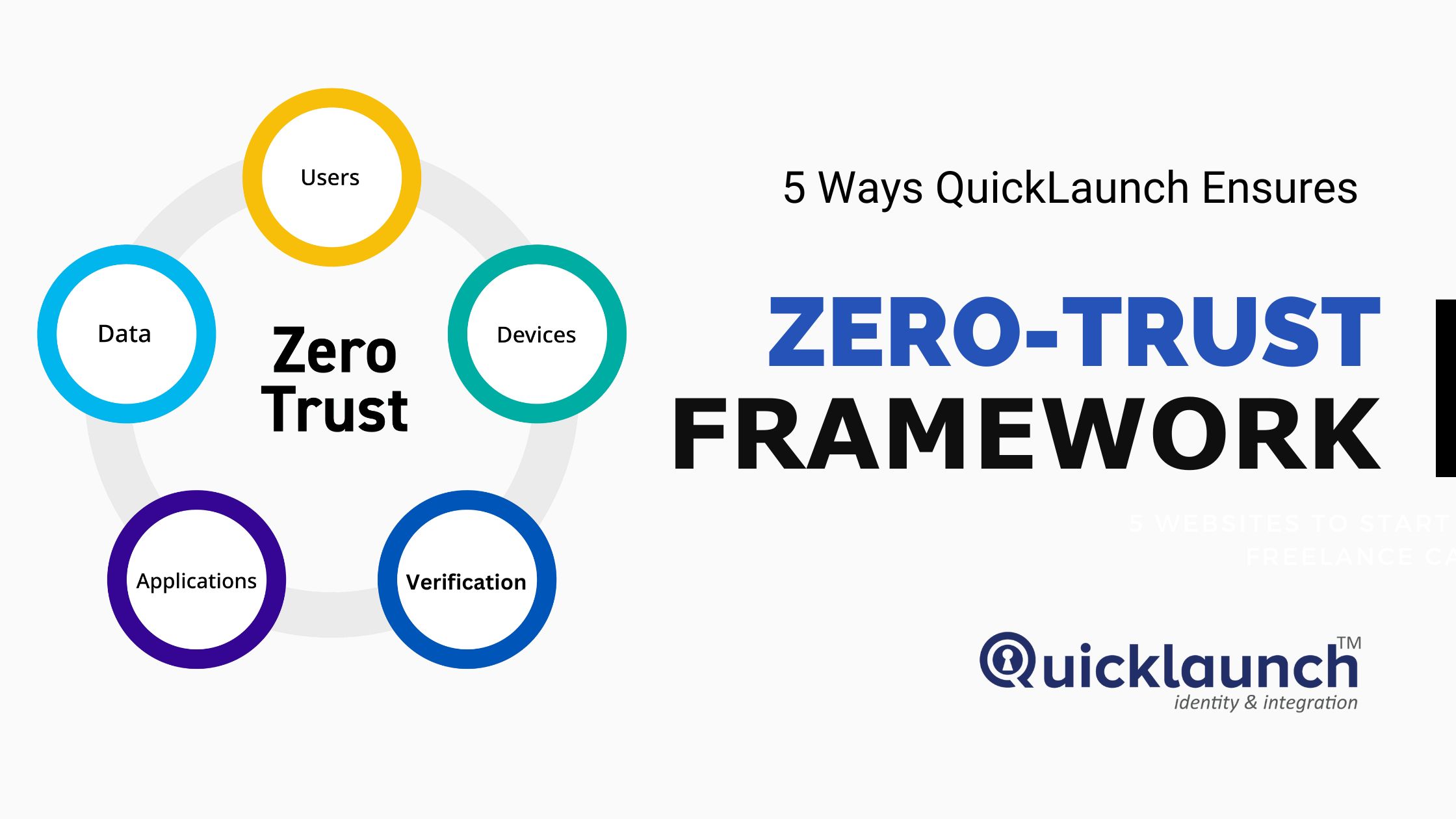
In today's tech-driven world, data is the backbone of any successful organization. If at risk of being exposed or stolen, it can cause irreparable damage to a company’s reputation and trustworthiness. That’s why organizations are now striving for safeguarded portals that guarantee their digital assets stay secure.
But the reality is not the same!
Gartner published a report in 2019 highlighting that “Zero trust is being misused as a marketing term. Vendors are applying the term ‘Zero Trust’ to market everything in security, creating significant marketing confusion.”
Let’s rewind this picture….
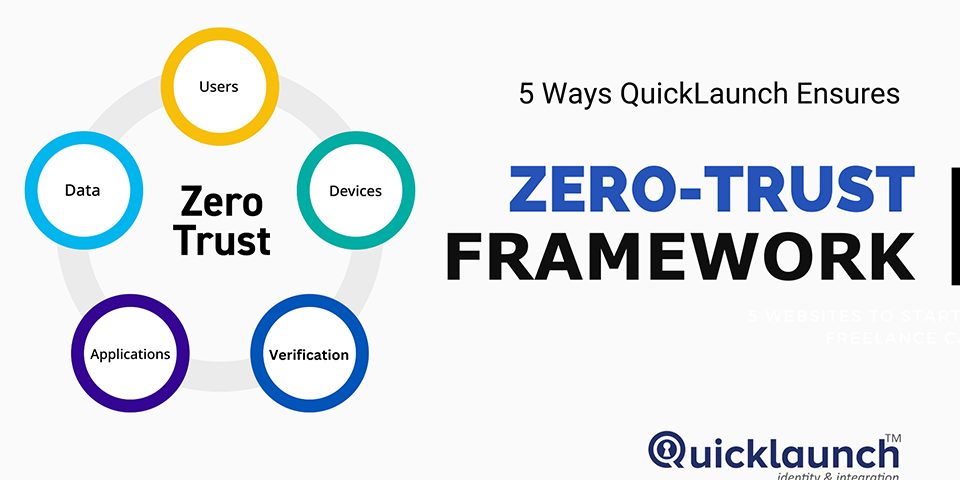
What exactly is the Zero-Trust Framework?
The idea behind zero trust is that no user or application should ever be trusted by default when it comes to protecting businesses in the cloud and mobile world. A crucial component of zero trust is least-privileged access, which establishes trust based on context (e.g., user identity and location, the endpoint's security posture, and the app or service being requested) with policy checks at each stage.
The top victims are the SMBs, education, and health sectors.
Why are they at the top?
SMBs, educational institutions, and health sectors house a lot of sensitive and business-critical data, including financial and personally identifiable information (PII), intellectual property (IP), and personally identifiable information (PII).
Who can safeguard them?
Organizations may not be able to prevent data breaches altogether, but they can take a giant step toward security with QuickLaunch. The global IAM provider offers companies the key to tackling digital transformation goals swiftly and efficiently--all while operating under a zero-trust architecture for optimal protection against any potential intrusions. With rave reviews from its customers, it's no surprise why so many turn to QuickLaunch as their go-to defense system in an uncertain world of cybercrime risks!
How is QuickLaunch going to defend them?
QuickLaunch is a global Identity and Access Management (IAM) provider that helps organizations speed up their digital transformation journey. Our powerful SSO portal simplifies access to applications, while our adaptive MFA ensures rigorous account security with passwordless authentication feature.
Why should you select QuickLaunch?
1. Reduce Internal Risk
QuickLaunch offers powerful identity attributes that guarantee secure communications between applications and services. What makes it truly remarkable is its adaptive Multi-Factor Authentication, a feature designed to curtail internal risk with push notifications, challenge questions, and role-based authentication. With robust security like this in place, companies can trust the integrity of their data and operations!
2. Recognizing suspicious geo-location
Security policies implemented with the use of geolocation detection criteria in a zero-trust security architecture provide a much safer environment for the system. This architecture helps to ensure that only authenticated users from approved locations are granted access to the system, keeping it secure from malicious activity. Additionally, with the use of geolocation detection criteria, this architecture can help to identify and block any suspicious activity taking place outside of the approved locations. By utilizing this type of security architecture, institutions are able to protect their systems from unauthorized access and potential threats.
3. Decrease the Risk of a Data Breach
Every entity is viewed as hostile, adhering to the principle of least privilege. Before "trust" is granted, each request is examined, users and devices are authenticated, and permissions are evaluated. Then, as the user's location or the data being accessed changes, this "trust" is continually reevaluated.
Without trust, a hacker who gains access to your network or cloud instance via a hacked device or other vulnerability won't be able to access or steal your data. Furthermore, the attacker won't have anywhere to go because the zero-trust model creates a "secure segment of one" with no way to move laterally.
4. Passwordless Authentication
Passwordless authentication allows a user to provide multiple, mutually independent proofs of identity without requiring a password to log in to the desktop, improving the user experience and reducing cyber-attacks. Moreover, there is no need to remember passwords every time, which reduces helpdesk calls.
5. Automated Provisioning
Automated provisioning—part of the identity and access management (IAM) and privileged access management (PAM) processes—is a crucial step when onboarding and offboarding employees. IAM platforms frequently provide automated provisioning as a feature because of its intended use, which is used by system administrators and IT managers to standardize provisioning rights based on roles and corporate policies.
In all, compared to the excessive privileged access of many flat network architectures, QuickLaunch offers superior visibility and control during audits or in the event of a data breach. At last, the QuickLaunch approach to cybersecurity applies security policy based on context established through least-privileged access controls and rigorous user authentication, rather than assuming trust.
Want to see how it works for yourself? Click here for a free trial