Access Any time. Anywhere. Any device.
Whether you're at home, in the office, or on the move, QuickLaunch ensures that you have secure and convenient access to everything you need.

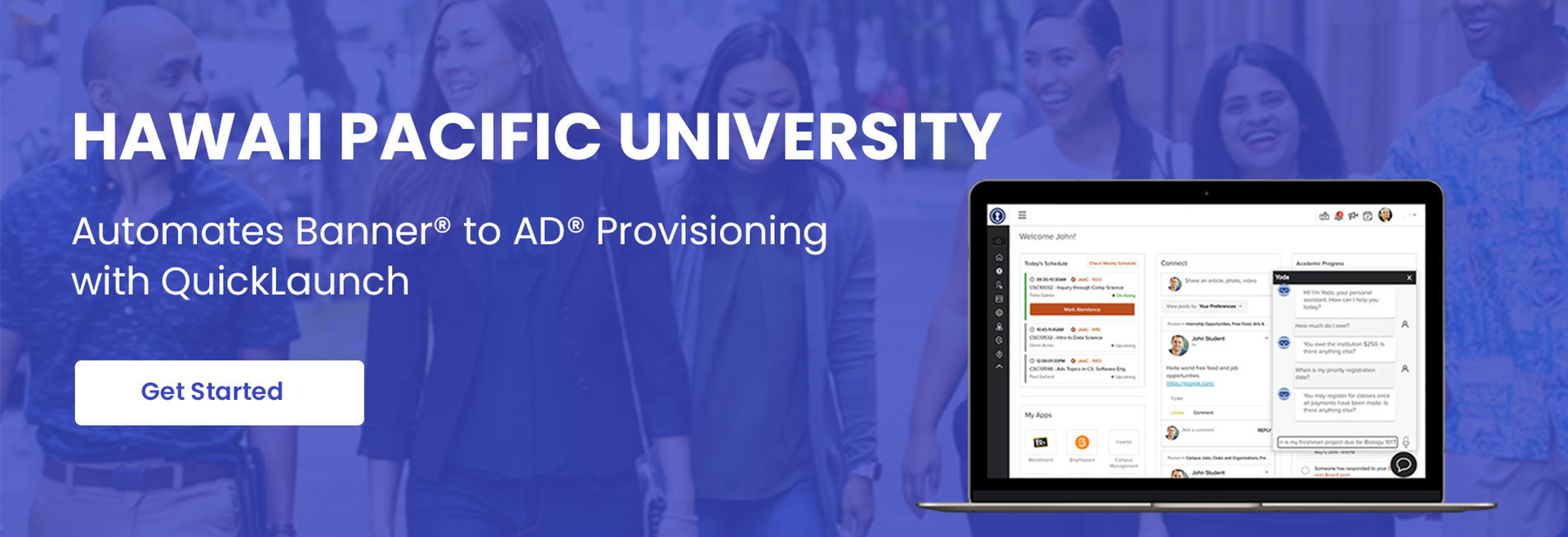
Automated Provisioning
Manage digital identities and onboard users on the fly by providing the right permissions in real-time
3M
Protected Users
500+
Customers
100M
Successful Authentications
99.99%
Uptime
Identity for Everyone
One platform to fulfill all your Identity Management needs.
Education
Keep your students, staff & faculty safe – with secure yet easy access to their apps. Our cutting-edge identity and access management ensures streamlined logins with multifactor authentication for ultimate security.
Learn more

Healthcare
Enhance the security of your patient portal and deliver a simplified secure experience to all stakeholders.
Learn more
Insurance
QuickLaunch's AI-powered cloud IAM solutions are built to cater to the modern needs of the Insurance sector, whilst complying with security requirements.
Learn more
The QuickLaunch Identity Platform
Safeguard your organization by securing your users’ identity. Work anywhere, on any device, with any application.
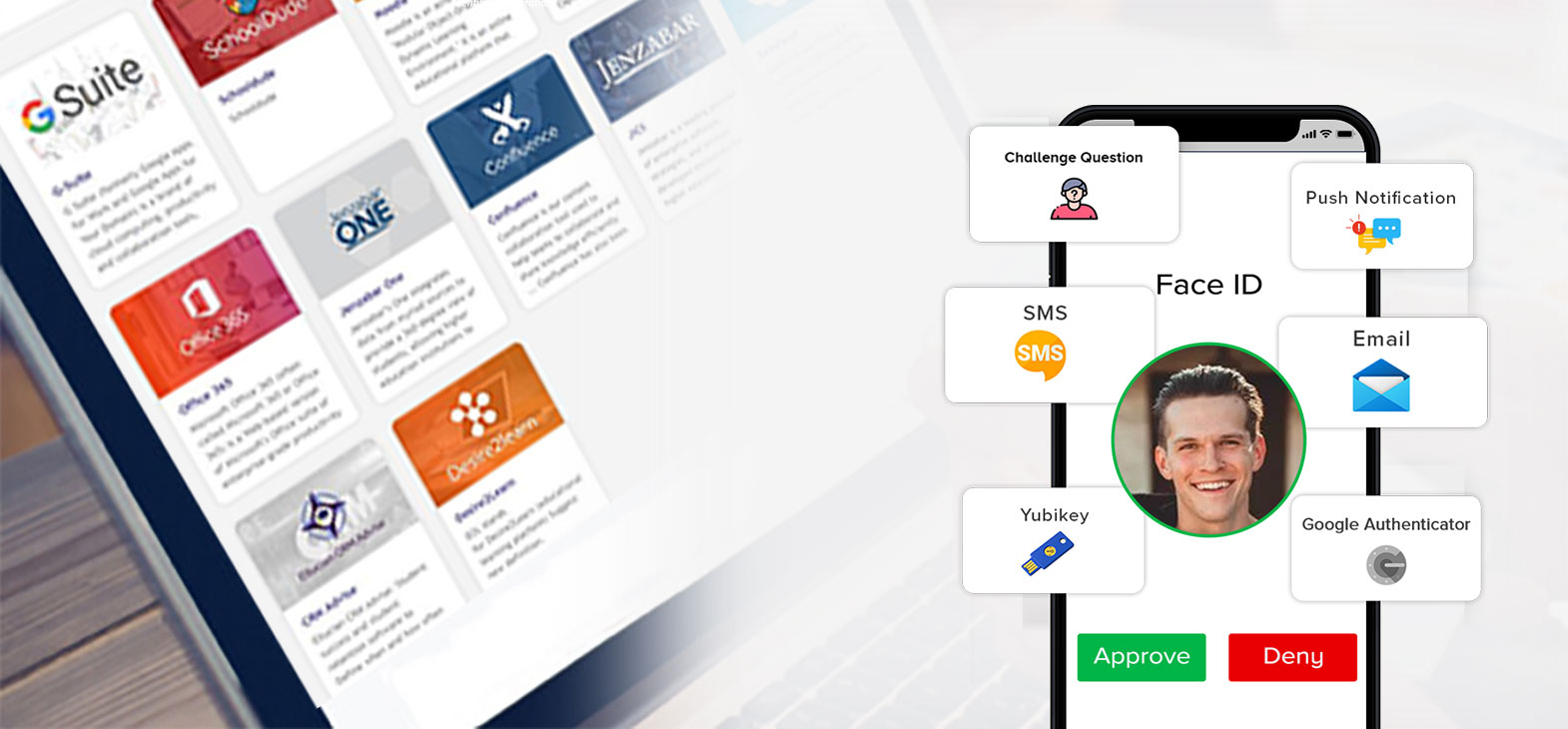
Workforce Identity Suite
Empower your end users to securely access the critical resources they need, wherever and whenever it suits them best— all from the convenience of any device.

For MSP/MSSP
Allow your clients to access an all-inclusive IAM solution quickly and conveniently by delivering QuickLaunch as a managed service. Empower them with a secure, reliable identity management solution that allows for the simple onboarding of users!